Ensuring that your Mendix applications are secure is a shared responsibility of Mendix and the customers using it.
Mendix is responsible for security of the platform and platform-supported content. Mendix Runtime protects your application and data according to your model. The Mendix Cloud handles security at the infrastructure level.
As a customer, partner, or Mendix Maker, you are responsible for security of the applications you build and manage on the Mendix platform. We have put together a list of five practical things you can do to make your Mendix application landscape more secure.
#1 Turn on Single Sign On (SSO)
Identity providers such as Entra Id (previously Azure AD) are centralized identity and access management solutions. They are more secure, more user friendly, and more efficient than the traditional username and password paradigm. Don’t we all love SSO! No need to remember another password, no more worrying if former employees could still login, and no more setting up password policies manually. So, don’t wait. Turn on SSO with Mendix now!
By setting up Single Sign-On in Control Center, you effectively delegate Mendix’s login experience to your identity provider. Go to Control Center → Security → Single Sign On tab, and connect your identity provider with Mendix. Follow the 3-step guided wizard and ta-da! Not only will the login experience become more secure and user friendly, it will also be in line with your enterprise standards. Enterprise Policies, such as 2FA and password reset frequency, that you set up in your identity provider will automatically apply to Mendix login experience too. It’s an easy way to up your game on platform user security. For more info, refer to this in-depth blog.
#2 Use modules such as SSO, SCIM, etc.
Complementary to platform users (aka makers who use Mendix platform to build and manage apps) are end users, aka the end users of your applications. A secure, seamless, and consistent login experience matters to end users as much, perhaps even more, than to platform users! So, how can you enable that?
It’s easy! Mendix provides a variety of pre-built marketplace modules to help. In line with the SAML 2.0 and Open Id Connect authentication protocols, Mendix provides SAML and OIDC SSO module. These modules allow your apps to delegate the login to an identity provider and achieve an SSO experience.
To go a step farther, you can also onboard/offboard users in line with your identity provider using LDAP or SCIM module. Select the login and user on/offboarding mechanisms based on your organizational policies, and advise all your makers to use these modules in their Mendix applications. You can also mark the chosen module as ‘Recommended’ using Marketplace Curation in Control Center. All the makers will know the organizational choice then.
#3 Subscribe to security advisories and set a security contact
Low-code platforms use reusable ‘building blocks’ to help accelerate rapid application development, for instance, the marketplace content. Over time, these building blocks/components may become affected by security vulnerabilities, thus impacting your application’s security. So, how do you stay secure? Mendix has you covered.
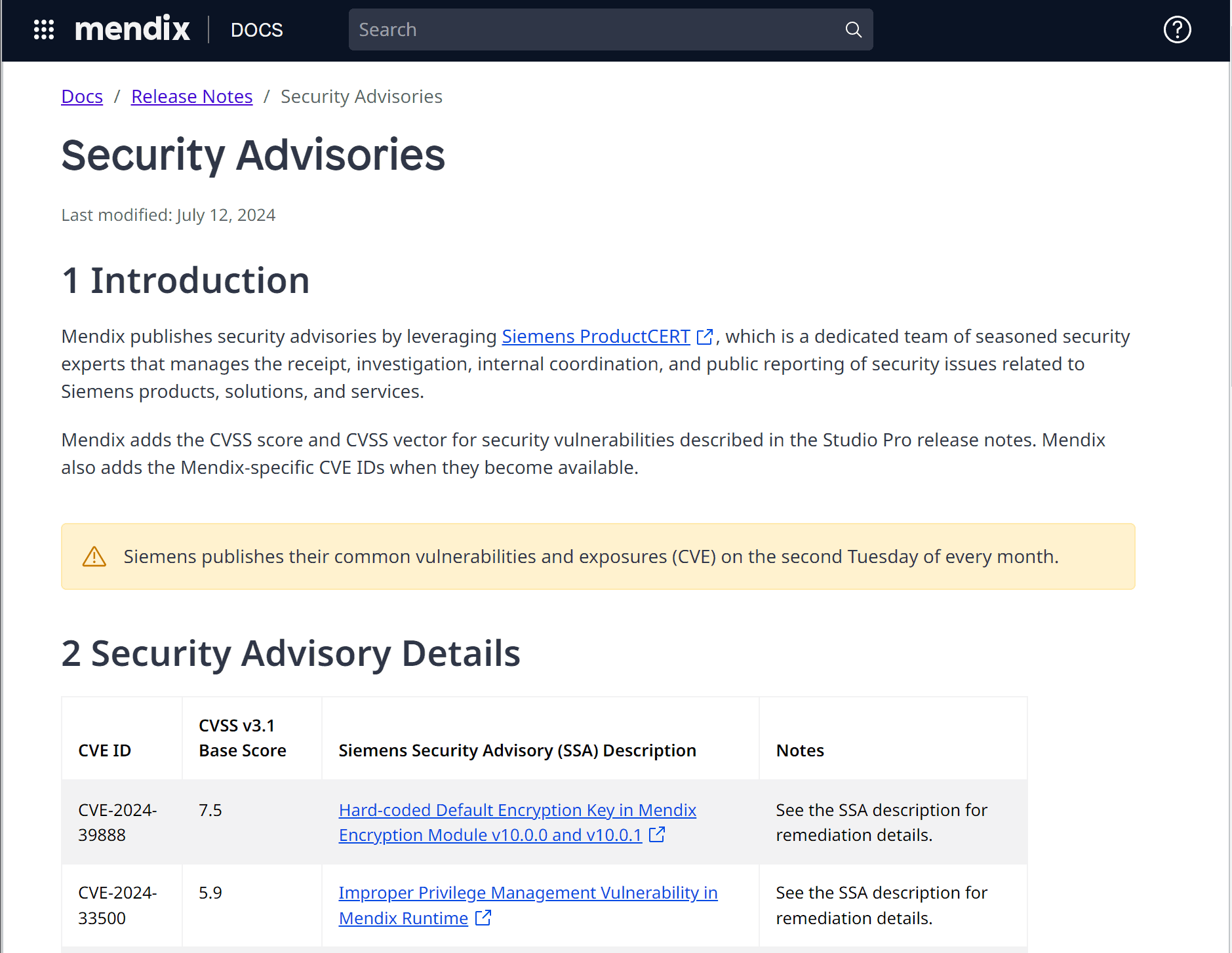
Mendix continuously monitors the platform and platform-supported components for security findings. If a vulnerability is detected, Mendix publishes security advisories. Mendix will provide a CVSS score and remediation guidance to fix the vulnerability. This typically involves upgrading to a higher version of the component to which a security fix has been applied.
These security advisories are published in the documentation, in Community Slack (#securityadvisories channel), and in RSS feeds. Subscribe to these to get notified immediately when a new vulnerability is detected.
Also, set up a basic vulnerability remediation process. Typically, it’s about vulnerability identification (which component became vulnerable), analysis (which apps are impacted and what’s the severity of impact), and remediation (how can I mitigate risk under SLAs set by the security team in the company).
Liaise with your IT and SecOps team to define a process. Additionally, you can also setup a Security Contact in Control Center who will be informed via email when a critical security vulnerability is detected.
#4 Use Software Composition
One fine day, you get notified of a security vulnerability with a score of 9 out of 10 on a marketplace component. Your next step: check if any of your Mendix applications use this marketplace component and, if so, how many apps? And which apps?
To perform this impact analysis, use the recently launched feature Software Composition. In Control Center, navigate to Software Composition > All Components tab, and view a list of all unique components used in the application landscape along with their usage across applications.
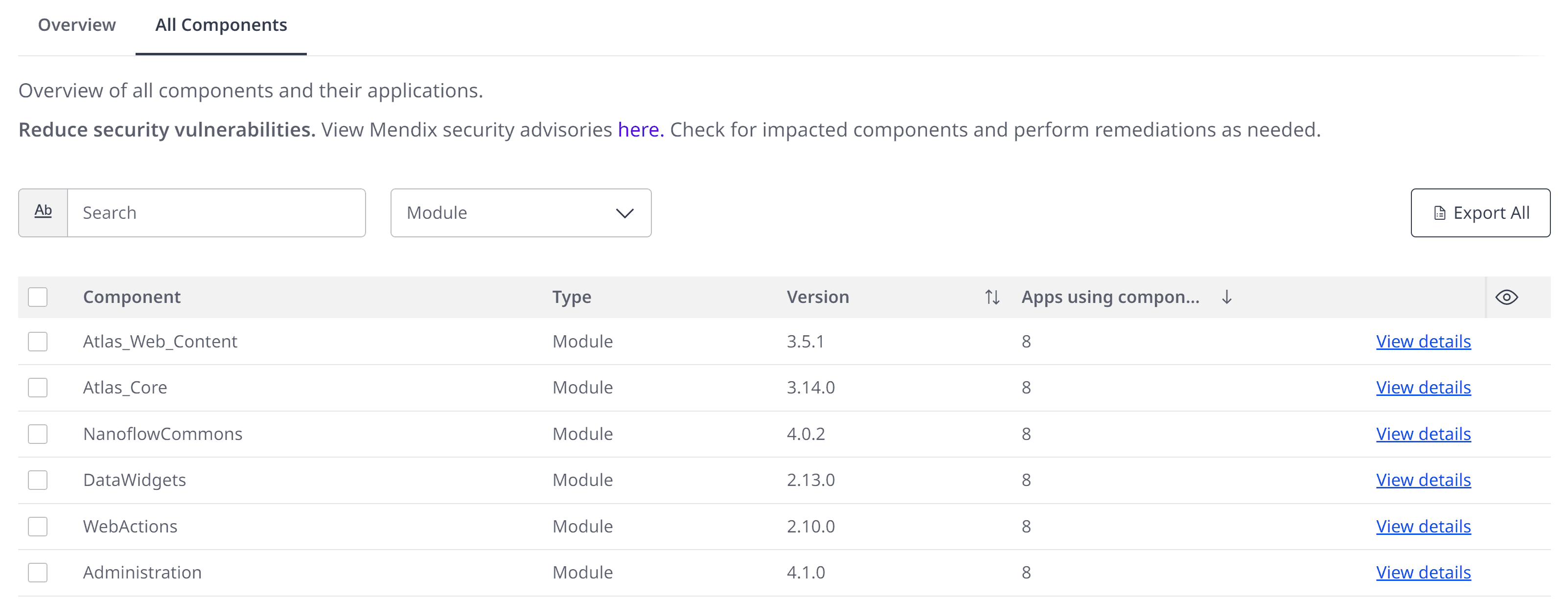
Next, view details of the components, view the impacted apps, and notify their technical contacts to make the necessary upgrades to mitigate the security risk posed by the vulnerability. Software Composition is also available in Mendix Portal, so makers have visibility too.
That’s it, a few simple steps that will help you secure your application landscape! Explore it today.
#5 Follow best practices for app security and anonymous user security
Application security and anonymous user security are two key aspects when building your applications in Studio Pro. When it comes to application security, a comprehensive list of best practices is available here. A few I’d like to highlight are as follows:
- Implementing access rules: This is an absolute hygiene factor. Access rules check if the user role has access to receive requested data.
- Using constants in your app: You may have sensitive credentials to be used in apps. To limit access to these, use constants which can be set per environment.
- Removing unused components and microflows in the app: Another hygiene factor, you should clean up elements of the model which are no longer being used. This will make it easier to maintain the app and reduce the risk of security vulnerabilities.
Next, let’s talk about anonymous users, i.e., end users who can access your Mendix application without any login or password. Imagine if you enabled anonymous users and provided them access to lots of entities in your domain model. By doing so, you are risking a malicious user potentially accessing sensitive data stored in the Mendix application. Hence, the general rule of thumb is to provide anonymous users as little access as possible. A comprehensive list of guidelines is available here.
So, don’t wait! Understand your share of responsibilities in creating a secure application landscape, and implement these tactical tips in motion if they aren’t already in place!
Helpful Resources:
- Mendix Academy Course – Configure advanced security
- Mendix certifications & more – Mendix Platform Security & Compliance | Mendix

